Automate and scale compliance, pain free
Get compliant without the chaos—Vanta automatically gathers the evidence you’ll need to get compliant, and continuously monitors your systems to make sure you stay compliant and secure.


The automated compliance solution for leading businesses





Spend 82% less time per framework and attestation related audit
IDC found that Vanta was able to help compliance teams save significant time through automation and continuous monitoring.

Every framework you need
Vanta supports [frameworks_count] leading security and privacy frameworks, like SOC 2, ISO 27001, HIPAA, and more (or customize your own). Plus, you can cross-map controls across existing frameworks, so you only do the work once.
more productive compliance teams 1

From reactive to real-time
Vanta takes you from point-in-time status checks to automated, continuous controls monitoring, giving you constant visibility into the health of your program. Connect the dots for your customers and demonstrate trust in real time by displaying passing controls on your Trust Center.

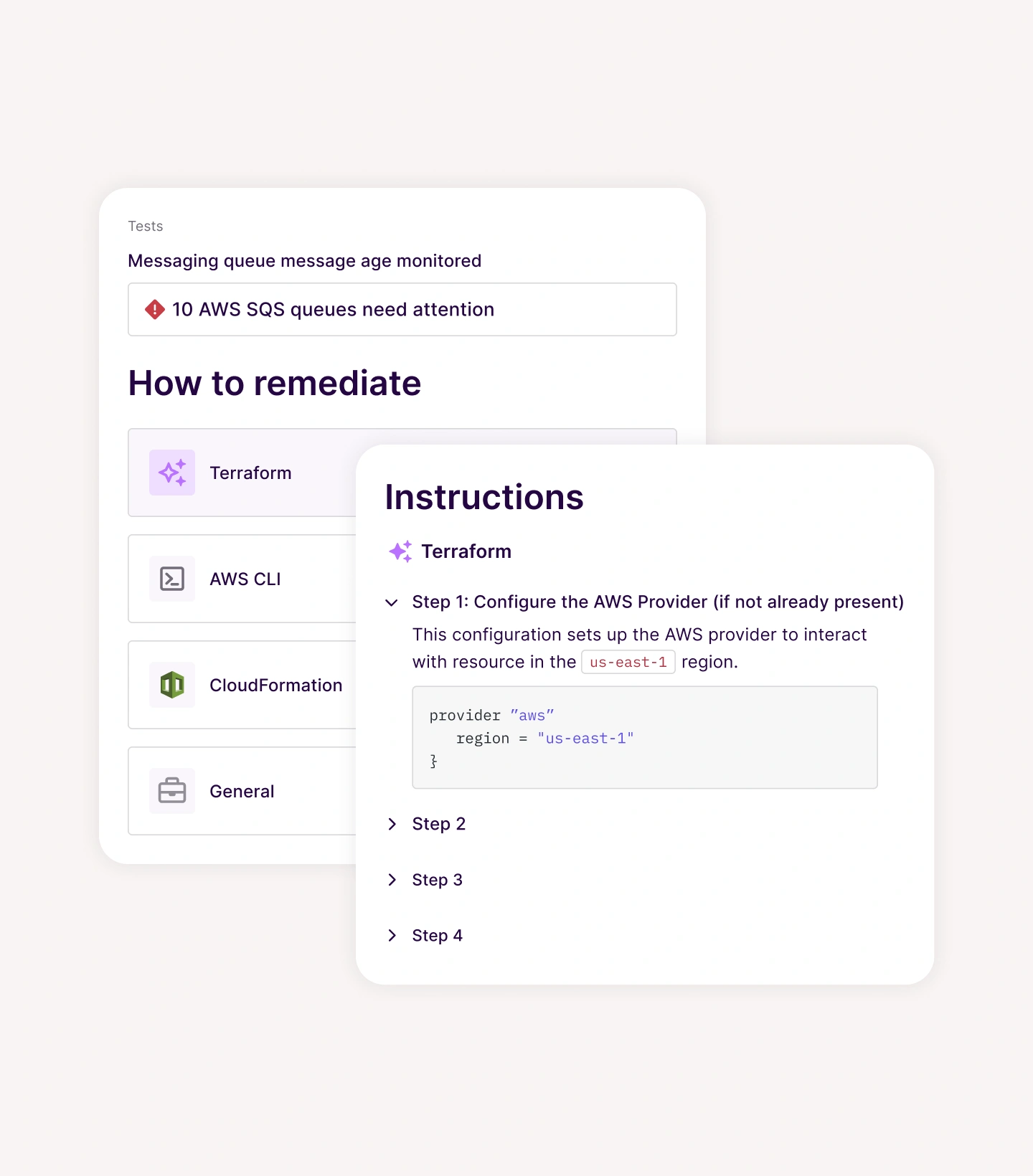
Actionable alerts, powerful remediation
1,200+ automated, hourly tests, powered by a market-leading ecosystem of [integrations_count] integrations, give you continuous visibility into your compliance posture, collect audit evidence, and allow for easy collaboration with your stakeholders. Plus, you can remediate issues faster with AI-generated code snippets, personalized to your infrastructure.
Everything you need to get compliant in one unified platform
Vanta provides the tools, partners, and expertise needed to take you from zero to compliant, fast. An in-app compliance roadmap guides you along every step, from first login to successful audit. Access the technology and service partners you need for things like penetration tests, cyber insurance, and background checks, all through Vanta.


Policy management
Simplify policy creation and management with templates for every framework, a step-by-step policy builder to guide customization, and automated employee acceptance tracking.

Personnel management
Ensure employees remain compliant with out-of-the-box security awareness training videos, in-app background checks, and customizable onboarding and offboarding workflows.

Pre-built and custom controls
Use our out-of-the-box controls or bring your own, and Vanta AI will map your custom controls to Vanta's library of automated tests, getting to continuous monitoring even faster.

Vanta partner network
Leverage Vanta’s extensive network of trusted auditors and partners to get the support you need. This includes vCISO services, managed service providers, complimentary penetration testing services, and more.

End-to-end audit support
Plan, prep for, and execute your audits, all within Vanta. Manage issues to track and resolve audit findings, and easily communicate with your auditor to stay ultra-efficient through the audit process.

[integrations_count] integrations
Vanta integrates deeply with tools ranging from cloud providers to task trackers to vulnerability scanners—and powers workflows like two-way task tracking, user access reviews, vulnerability SLA management, and more.
Learn more about automated compliance

Audit Ready Checklist
Get ready for your next audit with tips from Vanta’s team of GRC experts.

SOC 2 Compliance Checklist
Achieving SOC 2 compliance proves to your customers that you prioritize protecting their data. In fact, this proof of compliance helps your company to raise capital, sell to larger customers, and rise above the competition.

ISO 27001 compliance checklist
Our ISO 27001 compliance checklist will help simplify your path to compliance.
- IDC White Paper, The Business Value of Vanta (doc #US52656824), January 2025. Sponsored by Vanta.
















