Unlock government contracts with CJIS compliance
CJIS sets the standard for securing case files, biometric records, and other sensitive criminal justice data. Vanta simplifies the path to compliance with automated monitoring, guided workflows, and centralized control management, so you're ready for audits and RFPs.
The trust management platform powering security for over [customer_count] customers





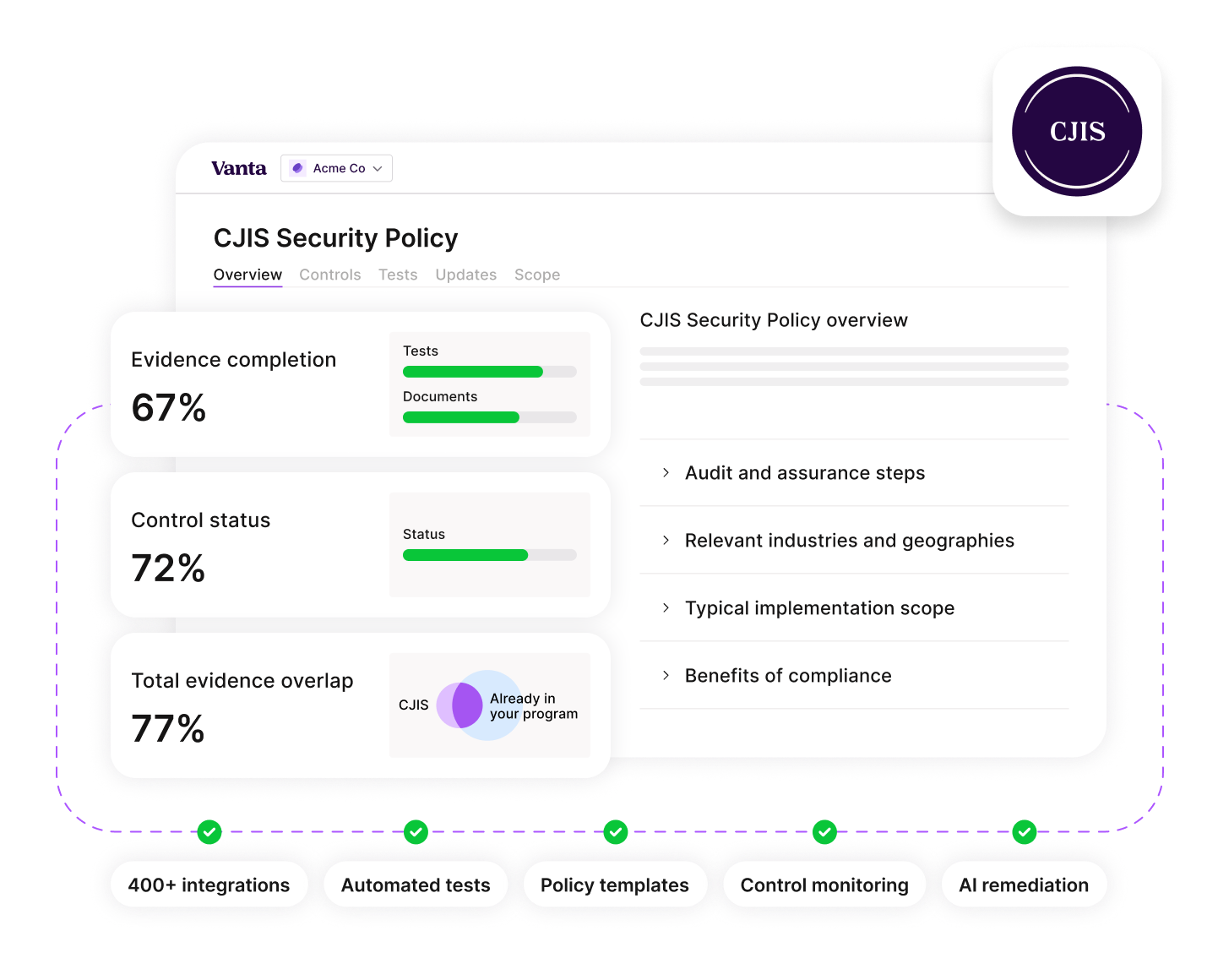
CJIS compliance, continuously
Surface issues in real time and stay ready for audits, without spreadsheets or manual trackers. Vanta automatically collects evidence and monitors key CJIS controls like access management, encryption, logging, and personnel screening.
Automated tests that monitor controls hourly, so you stay compliant every day—not just at audit time.
Integrations with your cloud, code, identity, and device tools for a complete, automated view of compliance.
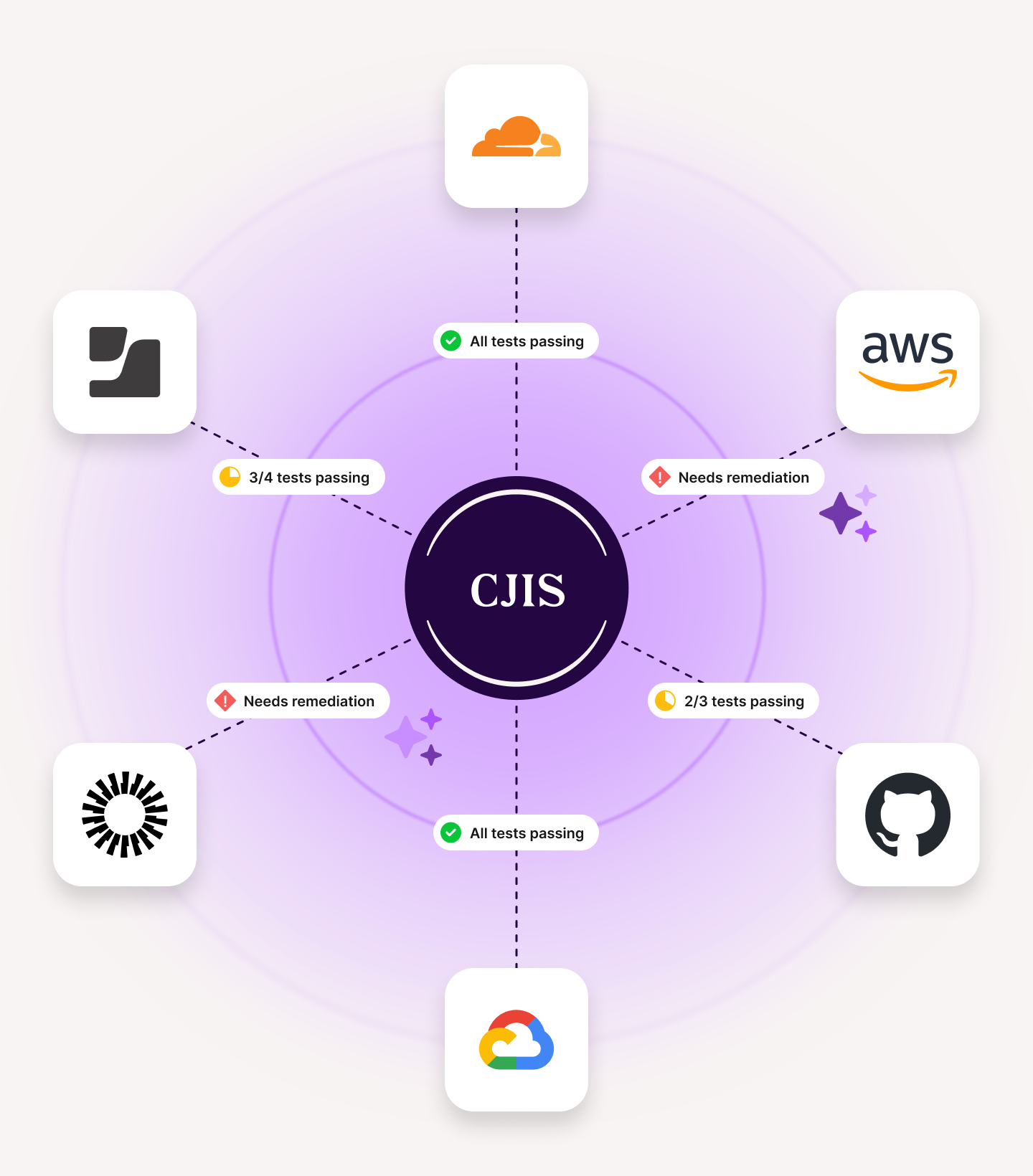
Guided, audit-aligned requirements
CJIS doesn’t have a central certifying body, so it’s up to you to interpret and apply the rules. Vanta breaks down complex requirements into clear, actionable tasks, so you know exactly what to do, when to do it, and how to prove it.
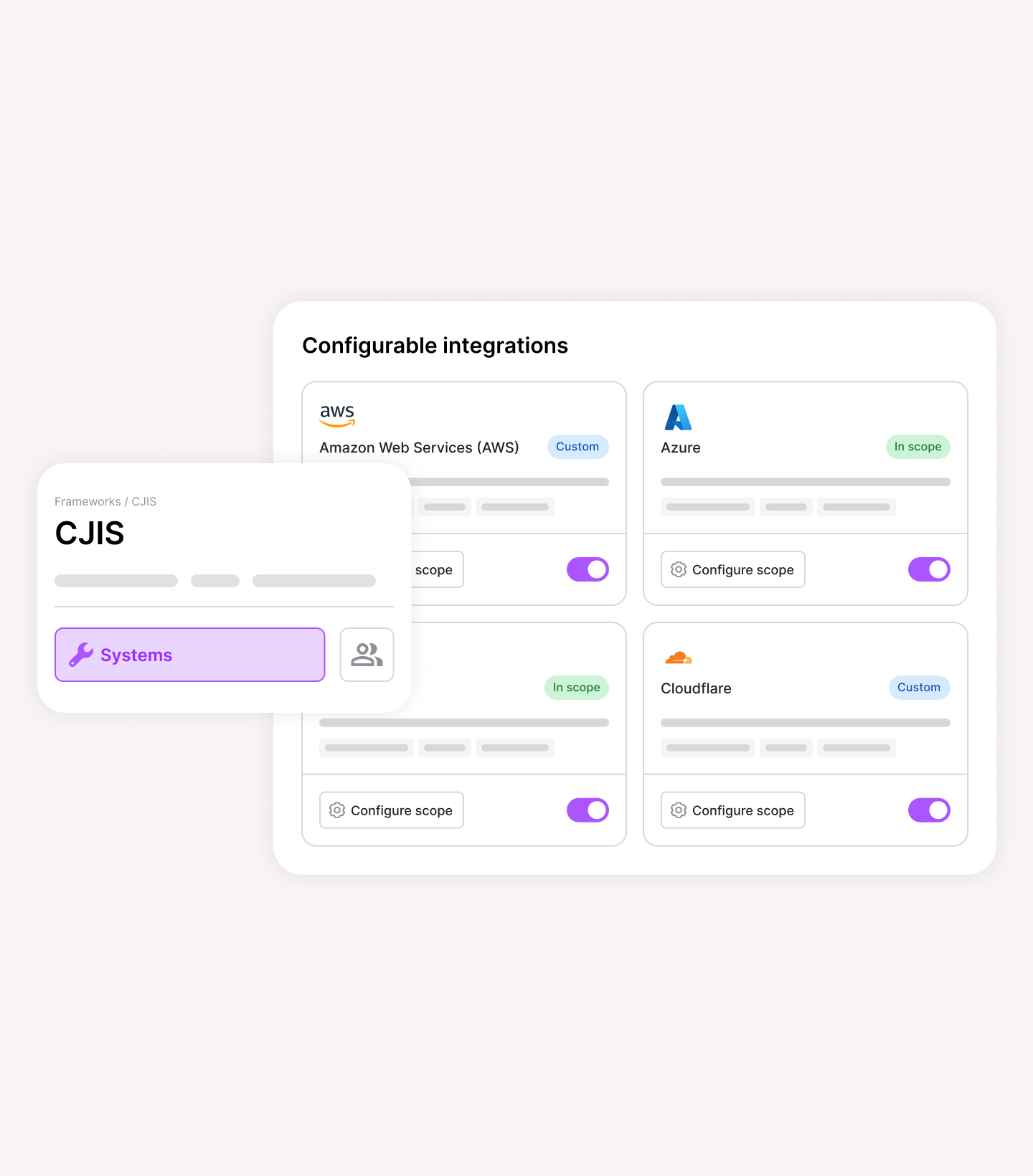
Scope CJIS to fit your organization
CJIS isn’t one-size-fits-all, and neither is Vanta. Define scope by business unit, product, geography, or framework. Vanta AI then tailors your policies, maps controls, and automates evidence collection, so your program reflects how your org actually operates.
On average, teams using the Vanta AI Agent save 4 hours per week.
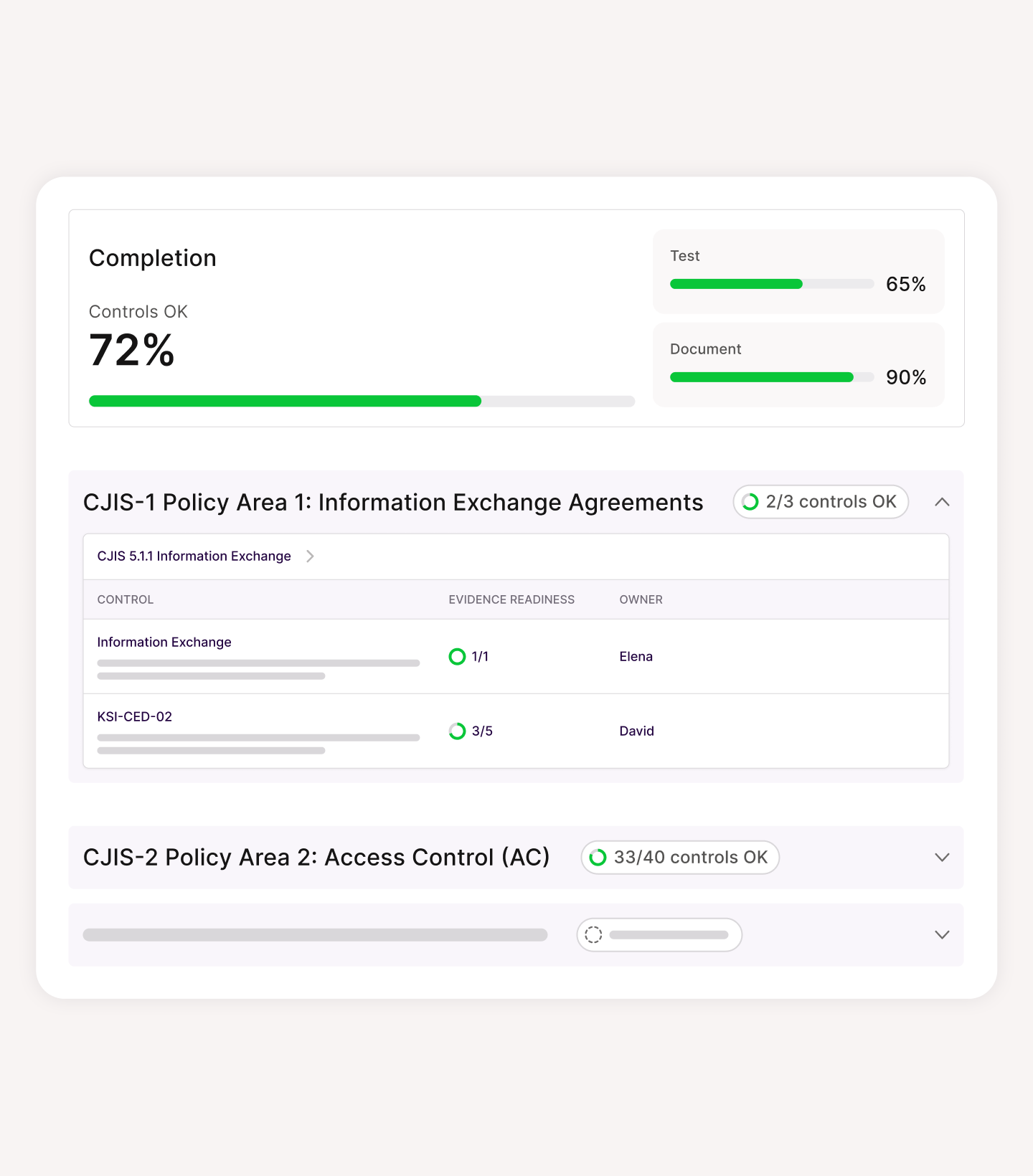
Work once, scale across many
See how much of each framework you’ve already covered so you can plan what’s next and move faster. Reuse work across SOC 2, ISO 27001, CRI, and more.
SOC 2
Prove to customers that you meet the industry standard for managing and protecting customer data.
ISO 27001
Meet global expectations with an auditable security program for managing information risk—especially for customers outside the US.
CRI Profile
Help financial service companies manage cyber risk by aligning to any of the four tiers in the Cyber Risk Institute Profile.
Additional features
Risk management
Assess your current posture, identify missing controls, and prioritize remediation, so you can reduce risk to Criminal Justice Information (CJI).
Centralized control management
Track the implementation, ownership, and real-time status of CJIS controls in one place. Stay organized and audit-ready.
Vendor management
Manage vendor risk by defining responsibilities, reviewing evidence, and ensuring third parties meet CJIS expectations.
AI-powered reviews
Use Vanta AI to highlight weak or missing evidence, summarize control gaps, and flag what needs attention, so you can move faster.
Issue detection
Continuously monitor for misconfigurations and control gaps, helping you resolve issues before they become blockers.
Access management
Eliminate identity silos and centralize your identity governance program in Vanta. Onboard, request, review, and offboard with ease.
Learn more about CJIS

The CJIS Security Policy checklist
A guide on how to achieve and maintain CJIS Security Policy compliance.

CJIS Security Policy compliance: An extensive guide
Find out who needs to comply, the policy’s 20 control areas, and the best practices to approach it.

Vanta’s Cybersecurity Maturity Assessment Template
Evaluate and improve your security posture with Vanta’s Cybersecurity Maturity Assessment Template—based on the NIST CSF 2.0. Track controls, score maturity levels, and build a scalable, resilient security program.
FAQ
CJIS is the FBI’s security policy for handling Criminal Justice Information (CJI). Any agency, contractor, or vendor that accesses, stores, or transmits CJI must align to the policy and demonstrate compliance to the relevant state or agency authority (CSA).
CJIS alignment is often a requirement for working with law enforcement and public safety agencies. Demonstrating compliance helps you win RFPs, speed up procurement, and maintain customer trust.
Yes. Vanta’s Third-Party Risk Management centralizes third-party assessments, evidence collection, and responsibilities, so you can ensure your vendors meet CJIS expectations.
Absolutely. Vanta maps overlapping controls across frameworks, so policies, tests, and evidence from SOC 2 or ISO 27001 can often be reused for CJIS, saving time and effort.
It depends on your scope and the agency’s requirements. Most orgs go through five phases: scoping, gap assessment, remediation, policy/training rollout, and continuous monitoring, often aligned to contract timelines or CSA reviews.









.png)
.png)
.png)